- September 12, 2024
- Posted by: SouTech Team
- Category: Blog
Introduction to DevSecOps and its Importance
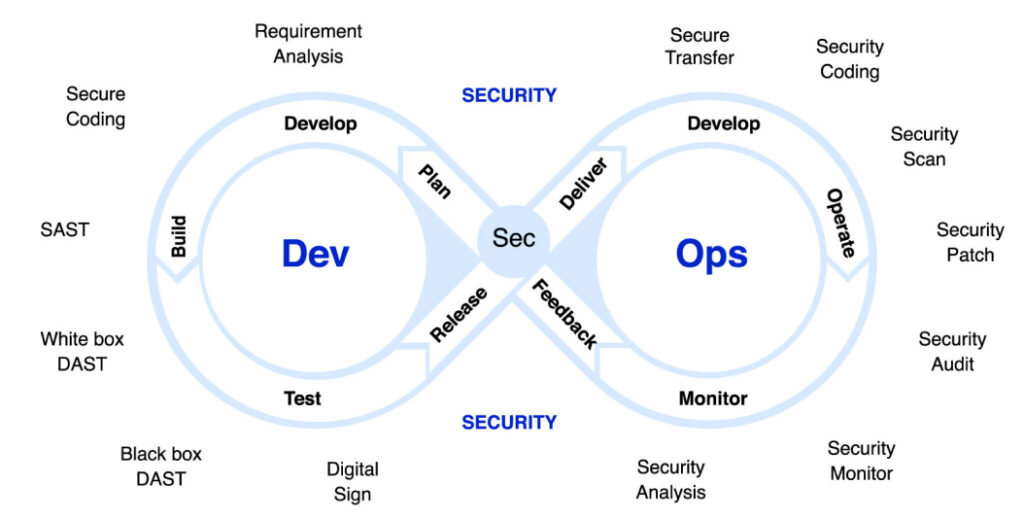
DevSecOps (Development, Security, and Operations) extends the principles of DevOps by integrating security practices into every phase of the software development lifecycle (SDLC). The goal is to ensure that security is not an afterthought but is incorporated from the beginning. Here’s why it’s important:
Key Concepts:
- Shift-Left Security: Moving security measures earlier in the development process. Traditional approaches often apply security at the final stages, but DevSecOps focuses on integrating security right from the planning and coding phases.
- Collaboration: Just as DevOps brings developers and operations teams together, DevSecOps integrates security teams with developers and operations to foster collaboration and shared responsibility.
- Automation: Automating security tasks (such as vulnerability scanning, compliance checks, and configuration audits) in CI/CD pipelines. This ensures that security processes are consistent, scalable, and less prone to human error.
- Continuous Monitoring: Real-time detection and remediation of security issues. By continuously monitoring systems, DevSecOps aims to minimize the window of vulnerability.
Why It’s Important:
- Speed Without Sacrificing Security: In fast-paced DevOps environments, security can sometimes be neglected to maintain speed. DevSecOps ensures you maintain security while keeping the pace of development and deployment.
- Cost Savings: Fixing vulnerabilities early in the development process is far cheaper than resolving security issues post-production.
- Compliance: Many industries have stringent security requirements (e.g., healthcare, finance). DevSecOps helps maintain compliance with regulations by automating security checks and audits.
2. Securing Infrastructure with Terraform
Terraform is an Infrastructure as Code (IaC) tool that allows you to define and provision infrastructure using declarative configuration files. It plays a critical role in DevSecOps by enabling you to incorporate security practices directly into the infrastructure provisioning process.
Key Concepts:
- Infrastructure as Code (IaC): Infrastructure is managed using code (scripts) instead of manual processes. With IaC, you can version control your infrastructure just like application code, improving transparency and collaboration.
- Security by Design: By using Terraform, you can ensure that infrastructure is created with security principles baked in. For example:
- Defining specific IAM roles and permissions to adhere to the principle of least privilege.
- Configuring secure VPCs, subnets, and firewall rules from the outset.
- Immutable Infrastructure: In DevSecOps, infrastructure should be immutable, meaning it is recreated from a secure, tested template whenever changes are needed. This minimizes security risks from unintentional changes or outdated configurations.
Security Practices Using Terraform:
- Role-based Access Control (RBAC): Use Terraform to define IAM roles and policies that restrict access to your resources based on user roles and responsibilities.
- Network Security: Ensure your Terraform configurations include secure VPC and firewall settings. You can restrict access to resources based on IP ranges, set up private subnets, and control ingress/egress traffic.
- Automating Compliance: Terraform can automate compliance by applying security policies and configurations consistently across environments (development, staging, production).
Example of Securing a Google Cloud Compute Engine Instance with Terraform:
You can use Terraform to define secure configurations for Compute Engine instances:
- IAM Roles: Assign the least privilege roles to your instance service account.
- Firewall Rules: Only allow necessary traffic (e.g., HTTP/HTTPS) and block all other ports.
- VPC Configuration: Use private IPs and create secure subnetworks for internal traffic.
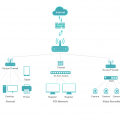
3. Basics of GCP Security: IAM, VPC, and Firewall Rules
Google Cloud Platform (GCP) provides robust security features that enable you to manage access control, networking, and traffic management at a granular level. These are essential components for any DevSecOps strategy when using GCP.
Key Concepts:
a. Identity and Access Management (IAM)
IAM is GCP’s system for managing access to resources. It lets you control who (users) has access to which resources and what actions they can perform.
- Roles and Permissions: GCP IAM uses predefined roles, which are collections of permissions to control access.
- Principle of Least Privilege: Always assign the smallest set of permissions necessary for a user to perform their job.
- Custom Roles: You can create custom roles tailored to specific security requirements.
- Service Accounts: These are special accounts for applications or virtual machines, used to interact with GCP services. Each service account can have its own set of permissions, which can be restricted using IAM policies.
b. Virtual Private Cloud (VPC)
A VPC is a virtual network that lets you isolate and secure your resources on GCP. It enables you to define networking and security boundaries, similar to on-premise networks.
- Subnets: You can divide your VPC into subnets, which can be used to isolate resources based on their function or security needs (e.g., internal vs external subnets).
- Private Google Access: Resources in a VPC can be configured to access Google services (like Cloud Storage) without requiring a public IP, improving security by limiting exposure to the internet.
- Peering and Interconnect: Use VPC peering or interconnects to securely connect your VPCs across different projects or organizations, without exposing them to the public internet.
c. Firewall Rules
Firewall rules control incoming and outgoing traffic to your instances. They are critical for protecting your resources from unauthorized access.
- Ingress and Egress Rules:
- Ingress Rules: Control incoming traffic to your resources. For example, you might only allow incoming HTTP (port 80) and HTTPS (port 443) traffic, blocking everything else.
- Egress Rules: Control outbound traffic from your instances. You might restrict outgoing traffic to certain IP ranges or ports to prevent data exfiltration.
- Stateless vs Stateful Rules:
- Stateless: Every packet is evaluated individually.
- Stateful: Evaluates traffic based on the state of a connection (e.g., established connections are allowed to communicate).
- Tag-based Rules: Firewall rules can be applied based on instance tags. For example, you can apply certain security rules to all instances tagged as “web-servers.”
Best Practices:
- IAM: Regularly audit IAM roles and policies to ensure there is no unnecessary access. Use predefined roles where possible.
- VPC: Segment your network using subnets and only expose public-facing services. Keep internal services isolated.
- Firewall: Implement a default deny-all rule and explicitly allow only necessary traffic. Regularly review and update firewall rules as your security posture changes.
Summary
- DevSecOps focuses on integrating security from the start of development, promoting collaboration, and automating security tasks.
- Terraform is an essential tool for automating secure infrastructure provisioning, allowing you to define IAM roles, secure networking, and automate compliance.
- GCP Security components like IAM, VPC, and Firewall Rules provide foundational tools to manage access, isolate resources, and control network traffic, all of which are critical to building secure applications and infrastructure.
Reach out for GCP DevSecOps Training and Solution