- August 10, 2023
- Posted by: team SOUTECH
- Category: Blog, Cyber-security and Ethical Hacking Training, Ethical Hacking and Kali Linux Free Training, Others, Security, Technologies
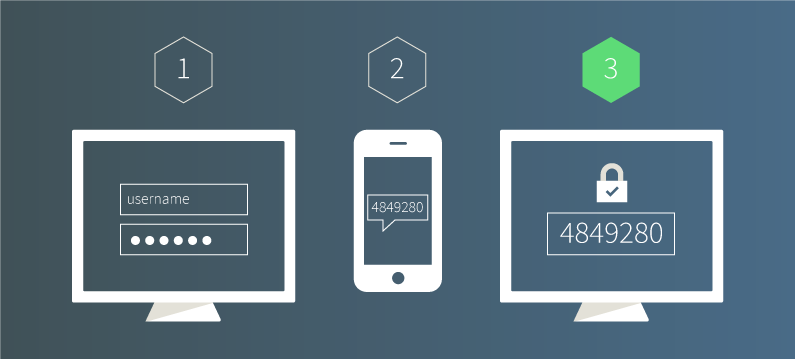
Two-factor authentication (2FA) is a security measure that adds an extra layer of protection to the login process. It requires users to provide two different forms of authentication, typically a password and a unique verification code sent to a trusted device, to verify their identity. This helps prevent unauthorized access even if the password is compromised.
Case Study: A company wants to enhance the security of their remote access system. The IT team decides to implement 2FA to strengthen user authentication. They select Google Authenticator as the 2FA solution and configure it on the authentication server. The team communicates the implementation to users, provides step-by-step instructions for enrolment, and conducts testing to ensure smooth implementation. Regular monitoring and user education ensure ongoing effectiveness and awareness of 2FA.
Step-by-step instructions:
1. Assess the authentication needs: Determine the systems or applications that require enhanced authentication security and evaluate the existing authentication methods in place.
2. Select a two-factor authentication (2FA) solution: Choose a 2FA solution that aligns with the organization’s needs, such as Google Authenticator, Authy, or Duo Security.
3. Configure the 2FA solution:
a. Install and set up the chosen 2FA solution on the authentication server or within the target systems.
b. Define user enrollment procedures to register and link their accounts with the 2FA solution.
4. Enable 2FA for users:
a. Communicate the implementation of 2FA to users and provide clear instructions on the enrolment process.
b. Guide users through the setup process, which typically involves installing a mobile app, scanning QR codes, or receiving one-time passcodes (OTPs) via email or SMS.
5. Test 2FA implementation:
a. Conduct thorough testing to ensure that the 2FA solution is functioning correctly and successfully authenticating users.
b. Verify that users can log in using their regular credentials and complete the additional 2FA step.
6. Educate users on 2FA usage and benefits:
a. Provide training materials or conduct awareness sessions to explain the importance of 2FA and how to use it effectively.
b. Highlight the benefits of 2FA, such as increased account security and protection against unauthorized access.
7. Monitor and maintain 2FA:
a. Regularly review the 2FA solution’s logs and reports to identify any abnormal activity or potential security incidents.
b. Keep the 2FA solution up to date with patches and security updates to address any known vulnerabilities.





