Blogging
-
Step by step guide on product design part 2
August 13, 2023 -
CISCO CyberOps lab – Tracing a Route; cybersecurity training
August 10, 2023 -
CISCO CyberOps lab – Incident Handling ; cybersecurity training
September 1, 2021 -
CISCO CyberOps lab – Regular Expression Tutorial; cybersecurity training
August 30, 2021 -
CISCO CyberOps lab – Encrypting and Decrypting Data Using OpenSSL; cybersecurity training
August 23, 2021 -
CISCO CyberOps lab – Hashing Things Out; cybersecurity training
August 23, 2021 -
CISCO CyberOps lab – Encrypting and Decrypting Data using a Hacker Tool; cybersecurity training
August 23, 2021 -
CISCO CyberOps lab – Social Engineering; cybersecurity training
August 20, 2021 -
CISCO CyberOps lab – Navigating the Linux Filesystem and Permission Settings; cybersecurity training
August 18, 2021 -
CISCO CyberOps lab – Locating Log Files; cybersecurity training
August 15, 2021 -
CISCO CyberOps lab – Getting Familiar with the Linux Shell; cybersecurity training
August 15, 2021 -
CISCO CyberOps lab – Working with Text Files in the CLI; cybersecurity training
August 12, 2021 -
CISCO CyberOps lab – Using Windows PowerShell; cybersecurity training
August 12, 2021 -
CISCO CyberOps lab – Extract an Executable from a PCAP; cybersecurity training
August 10, 2021 -
CISCO CyberOps lab – Investigating an Attack on a Windows Host; cybersecurity training
August 10, 2021 -
CISCO CyberOps lab – Incident Handling; cybersecurity training
August 8, 2021 -
CISCO CyberOps lab – Reading Server Logs; cybersecurity training
August 7, 2021 -
CISCO CyberOps lab – Attacking a mySQL Database; cybersecurity training
August 5, 2021 -
CISCO CyberOps lab – Exploring DNS Traffic; cybersecurity training
August 5, 2021 -
CISCO CyberOps lab – Class Activity – What’s Going On?; cybersecurity training
August 3, 2021 -
CISCO CyberOps lab – Anatomy of Malware; cybersecurity training
August 3, 2021 -
CISCO CyberOps lab – Using Wireshark to Examine Ethernet Frames; cybersecurity training
August 1, 2021 -
CISCO CyberOps lab – Introduction to Wireshark; cybersecurity training
August 1, 2021 -
CISCO CyberOps lab – Exploring Processes, Threads, Handles, and Windows Registry; cybersecurity training
July 30, 2021 -
CISCO CyberOps lab – Class Activity – Identify Running Processes; cybersecurity training
July 30, 2021 -
CISCO CyberOps lab – Create User Accounts; cybersecurity training
July 26, 2021 -
CISCO CyberOps lab – Windows Task Manager; cybersecurity training
July 26, 2021 -
CISCO CyberOps lab – Becoming a Defender; cybersecurity training
July 23, 2021 -
Stunning Aesthetics with CSS
July 18, 2021 -
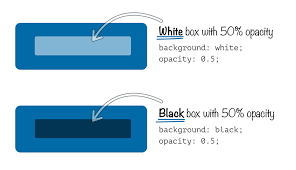
CSS color formats and alpha transparency
July 18, 2021 -
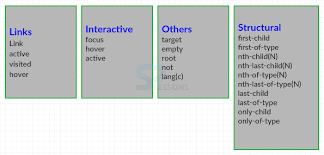
CSS structural pseudo-classes
July 16, 2021 -
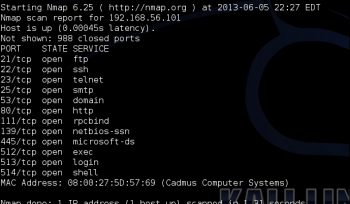
Checking for open port
March 3, 2021 -
Alexa Company Footprinting
February 26, 2021 -
Massive Discount on all our Trainings
January 11, 2021 -
Creating a brand strategy for individuals, small business and enterprise. Step by step guide
October 2, 2020 -
Android Users Advised To Delete These 16 Apps That Can Steal Texts And Contacts
September 29, 2020 -
CyberSecurity and Hacking
August 26, 2020 -
Biz Plans, Feasibility Report, Grants & Proposal Writing
August 26, 2020 -
Why content is the king?
August 25, 2020 -
WhatsApp Soundly Beaten By Stunning New Alternative
August 24, 2020 -
Native Mobile App Development
August 23, 2020 -
Human Resource Management
August 20, 2020 -
Graphics, Branding, UI/UX Design Professional
August 18, 2020 -
MEGA REWARD FOR SOUTECH FACEBOOK TOP FANS!
August 9, 2020 -
Integrating Blogging into a Business Strategy
July 20, 2020 -
Affiliate Marketing Overview- Infographics – Digital Marketing Training Nigeria
May 30, 2020 -
WordPress Subdomain | How To Install WordPress On Subdomain? SOUTECH Hosting
October 19, 2019 -
Enumeration Using SoftPerfect Network Scanner Tool
October 16, 2019
- 1
- 2