- August 12, 2017
- Posted by: cyberanalyst
- Category: CISSP, Consulting, Cyber-security and Ethical Hacking Training, Development, Others, Project and Research Nigeria, Softwares, Technologies, Website Design Service Abuja
Vulnerabilities in softwares have been widely discussed and looking at it from the human perspective, human emotions play a large part. Anytime someone is faced with a scary or frightening scenario, their first reaction to it matters a whole lot.
Social engineers leverage on this type of vulnerability to launch successful attacks on victims. I am going to discuss in details what social engineering is all about and its different forms as this particular vulnerability stands at 80% when it comes to the techniques which cybercriminals perpetrate attacks.

What is Social Engineering?
Social engineering is a technique whereby cybercriminals make use of human interactions to trick users into giving out sensitive information such as personal credentials.
| Want to start an eBusiness and Grow it Globally with free IT, Legal, Internet Discounts,3 Months SME Startup Course, ePayment Integration, Biz Development Services, Free Website, Free SMS Units/Portal all done for you within 30 Days?
Start Here>> Click >>> Start a Digital Business in Nigeria
Types of Social Engineering
The fact that social engineering leverages on the human nature and emotions to perpetrate, attackers have deployed many techniques to trick users both online and offline. Here are a few techniques you should know about;
Phishing:
Phishing is one of the oldest cyber tricks and has been grown to be one of the most popular most successful means of exploiting computer users. In phishing, cybercriminals usually attempt many tricks and methods to get information from you. Recently, they have resorted to using scare tactics which can come in form of an urgent situation which requires your attention usually having to do with your banking details or your other online accounts. Users therefore will have to make decisions based on fear and how they feel at the time the scenario is simulated.

Emails that seem to be from a legitimate authority such as your financial institution or your company will be sent to you requesting your username or password in order to get login access. Normally, people tend to react to when issues involving their finances or jobs are involved especially when it appears to come from a higher management. I will reiterate that one major phishing tactic is in the sense of urgency applied to these messages. I have written comprehensively on the forms and techniques of phishing so you can look it up. Read more on phishing
Baiting
Now let’s look at this technique which involves cybercriminals leaving a malware-infected USB or external devices in a public or open place. They leverage on the curious nature of humans such that when someone out of curiosity picks up this device and plugs it onto their computer systems in order to see what information is on it. Once they do this, the malware automatically gets injected into their computers.
Pretexting
In pretexting, the cybercriminal fabricates some very emotional stories and scenarios that tend to get to the emotions of their victims. Sometimes the stories can come in form stories of being stranded in a foreign country and sometimes can be that they are princes or princesses in their countries and their Father just passed away. They then try to tell the victim to please help them with a sum of 500USD or more in order to take back the throne. Like I said, these type of scenario tends to get to the emotions of victims who may always want to help. Pretexting is used alongside other methods as most of the techniques are targeted towards getting to the emotions of the victim or the cybercriminal attempts to impersonate someone on the telephone.
Hacking Emails and Spamming of Contacts
It is in the human nature to be inclined towards the affairs of their family and people they seem to know. For example, if my brother sends me an email message that comes with a subject that says “Look up this website, you may find something of interest” I normally wouldn’t resist checking it out by clicking open. Now this is the reason why a cybercriminal will try to leverage on this technique by using emails addresses and passwords. Immediately the victim’s personal credentials are obtained by the cybercriminal, they are take total control of the users account and will further more spam all the contacts that are on the users’ list. Always remember that the main objective of this attack vector is to spread malware with the desire of tricking people into giving out their personal data.
Vishing
This technique of all the methods mentioned so far and beyond involves the most of human interactions. In vishing, the cybercriminal puts a call through to an employee of an organisation faking to be a trusted individual to the organisation. They can pose to be a representative from the bank or other highly profiled company’s related to the organisation of the victim proposing to do a business with them.

Their aim is to try to get as much information as possible from the victims. They can even pose to be a fellow employee with a lost or misplaced password and request for their passwords and may try to sound legitimate by asking questions to verify the identity of the victim.
Quid Pro Quo
This is also referred to as something-for-something. This technique involves attempting to entice users with winning prizes, products or getting discounts on purchase of expensive products. This scam is fashioned such that the users can only get something only after they have completed a form which requires mostly your personal data. The information gathered can then be used to perpetrate other attacks such as identity theft etc.
Spear Phishing
This is a technique that is related largely related to phishing and can be referred to as phishing’s complex cousin. In spear phishing, the cybercriminal targets the employees of an organisation and does some reconnaissance on them online with the aim of getting personal information.

Information can be gotten from internet searches and social media platforms via profiles. Once they have been able to get details personal to them, they can then start sending emails that may seem very necessary and of interest to them in order to entice them. Such that once they click the links sent to them, the malware file attached can be downloaded to their system. Once the cybercriminal successfully tricks the user, the malware is installed on the user’s computer which can be spread throughout the network to other computers on the company network.
Farming
This is more like a long-con where the cybercriminal tries to establish a relationship with a target. They usually go through their targets social media profiles in order to establish a relationship and gather as much as information that will help them perform an attack.
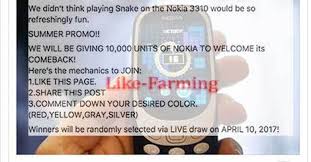 This attack form typically depends on pretexting because the attackers aim is to have prolonged conversations with the target in order to extract as much information as possible.
This attack form typically depends on pretexting because the attackers aim is to have prolonged conversations with the target in order to extract as much information as possible.
Hunting
This is a shorter version of all the attack forms. The cybercriminal will typically use baiting, phishing and email hacking to extract information from a chosen target passively (i.e. with no direct contact or with little interaction as possible).
Social engineering has taken over all forms, both online and offline and therefore has become very difficult to control or cut off its threats. Therefore, your best defense mechanism against social engineering is to educate yourself and your employees if you run an IT-driven organisation. You should also be aware and lookout for any possible attack methods that may come.
We have a comprehensive course that can help you learn more on how to protect yourself from social engineering and other attack forms. Subscribe to our CEH course today in SOUTECH.
| Want to start an eBusiness and Grow it Globally with free IT, Legal, Internet Discounts,3 Months SME Startup Course, ePayment Integration, Biz Development Services, Free Website, Free SMS Units/Portal all done for you within 30 Days?
Start Here>> Click >>> Start a Digital Business in Nigeria

