- July 17, 2017
- Posted by: cyberanalyst
- Category: CISSP, Cyber-security and Ethical Hacking Training, Softwares, Technologies
I will define phishing as an online con game where a cyber criminal disguises as a trusted entity and attempts to obtain sensitive information such as passwords, user account names, credit card credentials from a user via email which is often for malicious purposes.
 A person who takes part in this sort of crime is known as a phisher. To throw more shade, they can use SPAM, email messages, malicious websites as well.
A person who takes part in this sort of crime is known as a phisher. To throw more shade, they can use SPAM, email messages, malicious websites as well.
So How Do You Know It is a Scam?
Phishing can take different forms where the cyber criminal may trick you by luring you into giving them your personal details via
- Social media messages (Whatsapp, Facebook, twitter, LinkedIn, etc.) and other popular sites like dating sites.
- IMs
- Text messages
- Internet Chat rooms.
| Want to start an eBusiness and Grow it Globally with free IT, Legal, Internet Discounts,3 Months SME Startup Course, ePayment Integration, Biz Development Services, Free Website, Free SMS Units/Portal all done for you within 30 Days?
Start Here>> Click >>> Start a Digital Business in Nigeria
Sometimes they can go to the extent of luring you to install a malicious software or program often known as spywares. These spywares have background payloads which can track and record your passwords and other information you may enter on your computer through keyloggers.
I’ll list a few warning tips and signs you should look out for as concerning Phishing;
- Phishers always disguise to be legitimate companies and use emails to request for your personal information and they have people on standby to respond through their malicious websites. They have been known to always make use real company logos and slogans and often a spoofed email address.
- These emails may take the form of a message from your bank, a customer care agent or help desk support soliciting for money.
- Often times they can use a call to action which you may get that your account has been shut down and that you need to log in your details immediately in order to stop it from happening. They may also demand for your personal information so they can verify your identity.
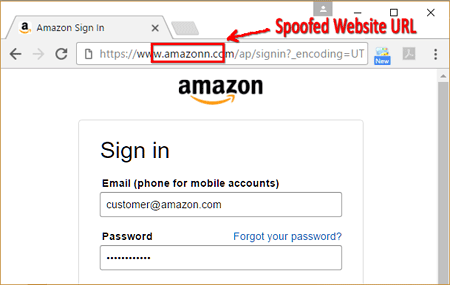
- The phishing websites can look very original and remarkably legitimate because they make use of copyrighted images from the original websites belonging to the organization.
- If you look at the URLS and messages, you will notice they are often bogus or being misspelt including the company names.
Phishing Countermeasures
So now that you know the various forms in which Phishing can take, I’ll explain in just a few tips how to stay protected.
- The first thing to do when you receive any emails from your financial institution, check the URL of the website, copy it and paste in your browser and ensure it https:/ verified at the beginning of it in the task bar. https means it is a protected or secure website.
- Always check the email header example to know the sender of the mail and other details you can capture from the header. I’ll use Gmail for instance to demonstrate to you how to check the email header.
Login to your Gmail>>Open the message>>Click on the dropdown button close to the reply tab>>Click on “Show Original”
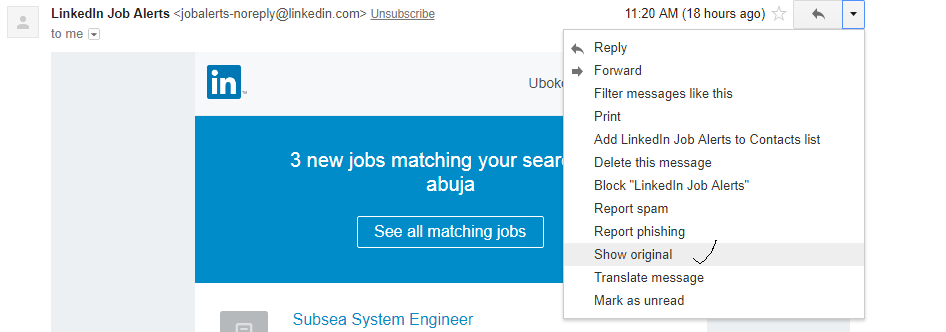
When you do this, you can see the header. Other email platforms have their own paths to get to the headers. You can do a little research on it if you are a yahoo, Hotmail etc. users.
You can boycott all these procedures if you just need the email id by just checking the top of the email to take note of the email id.
- Do not give out any of your personal information via email, social media chatting platforms, text messages or instant messaging platforms.
- Some financial institutions send monthly review of your account statements and require that you download and view them. Criminals also take this form to send programs that have keyloggers and spywares attached to them.
So, do not download any program or file from a suspicious email. You can as well block them.
To block any suspicious mail also using Gmail as template;
Login to Gmail>>open the message>>Click on the dropdown button close to the reply tab>>Click on Block
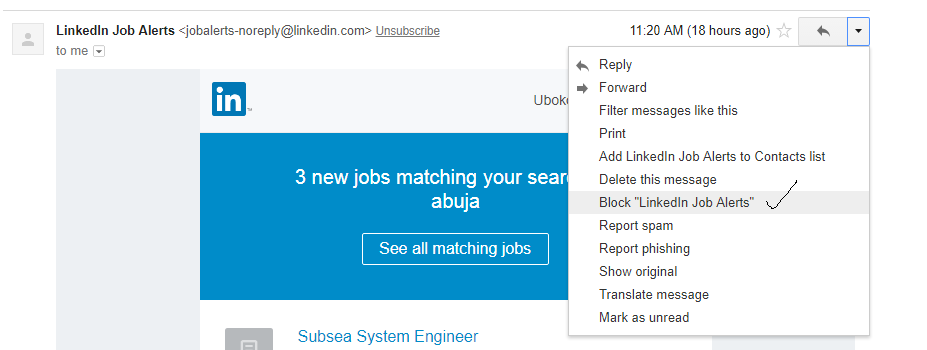
Remember to always stay protected, stay alert against all forms of online malicious threats. Stay glued to our well-informed journals to get more tips on how to stay protected. You can subscribe to our Ethical Hacking course in SOUTECH ventures to get more grounded information on Internet security.
| Want to start an eBusiness and Grow it Globally with free IT, Legal, Internet Discounts,3 Months SME Startup Course, ePayment Integration, Biz Development Services, Free Website, Free SMS Units/Portal all done for you within 30 Days?
Start Here>> Click >>> Start a Digital Business in Nigeria

