- September 12, 2023
- Posted by: SouTech Team
- Category: Blog
Step 1: Installation of Wireshark
- Download Wireshark:
- Visit the official Wireshark website at https://www.wireshark.org/download.html.
- Download the appropriate installer for your operating system (Windows, macOS, or Linux).
- Install Wireshark:
- Windows: Run the downloaded .exe file and follow the installation wizard instructions.
- macOS: Open the downloaded .dmg file and drag Wireshark to the Applications folder.
- Linux: Follow the installation instructions for your specific Linux distribution.
Step 2: Launching Wireshark
- Windows and macOS:
- Launch Wireshark from your applications or desktop shortcut.
- Linux:
- Open a terminal window.
- Type
wiresharkand press Enter to start Wireshark with administrative privileges (usually requires root or sudo access).
Step 3: Capturing Packets
- Select an Interface:
- Wireshark will display a list of available network interfaces. Choose the one you want to capture traffic on (e.g., Ethernet, Wi-Fi).
- Start Capture:
- Click the “Start” button to begin capturing network traffic on the selected interface.
- Capture Filters (Optional):
- Use capture filters to specify which traffic you want to capture. Filters can be based on protocols, IP addresses, ports, and more.
- Stop Capture:
- Click the “Stop” button to halt the packet capture when you’ve captured enough data.
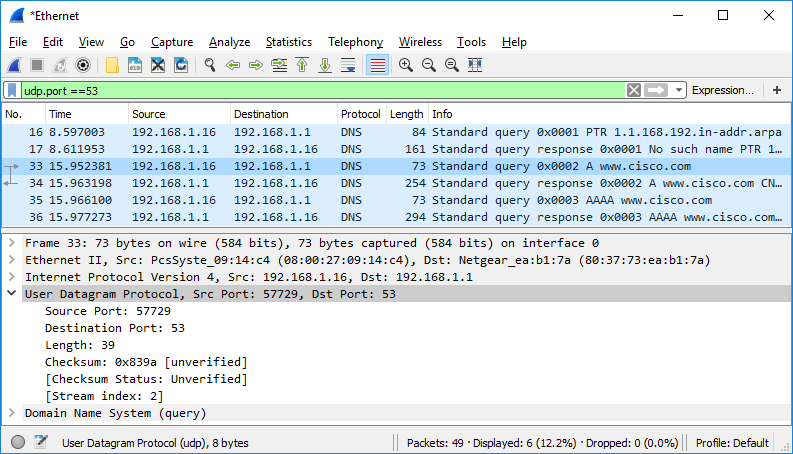
Step 4: Analyzing Packets
- Packet List Pane:
- The main window displays a list of captured packets. Each row represents a packet and provides information like source and destination addresses, protocols, and time.
- Packet Details Pane:
- Click on a packet in the list to view detailed information about that packet in the lower pane. This pane shows the various protocol layers and their contents.
- Colorization:
- Wireshark colorizes packets to help you quickly identify issues. Green packets indicate normal traffic, while other colors may indicate potential problems.
Common Use Cases:
- Troubleshooting Network Issues:
- Wireshark is a powerful tool for diagnosing network problems, such as slow connections, dropped packets, or abnormal behavior.
- Security Analysis:
- Detect and investigate security incidents, including intrusion attempts, malware infections, and unauthorized access.
- Performance Optimization:
- Analyze network performance to identify bottlenecks, latency issues, or inefficient protocols.
- Protocol Analysis:
- Understand how different network protocols work and how devices communicate on your network.
- Forensic Analysis:
- Use Wireshark to collect evidence during digital forensics investigations.
Interpreting pcap Files:
- Open pcap Files:
- To open a pcap file, go to “File” > “Open,” and select the desired file.
- Filtering Packets:
- Apply display filters to focus on specific packets or types of traffic within the pcap file.
- Follow TCP Stream:
- Right-click on a TCP packet and select “Follow” > “TCP Stream” to view the entire conversation between two endpoints.
- Statistics and Analysis:
- Explore the “Statistics” menu to access various analysis tools, such as endpoint statistics, protocol hierarchy, and conversation lists.
- Exporting Data:
- Export captured packets or specific analysis results in different formats, such as CSV or plain text.
Wireshark is a versatile tool, and its capabilities extend beyond this basic guide. As you gain experience, you can explore more advanced features and use cases, such as scripting, custom dissectors, and expert analysis.
Start your cybersecurity career TODAY!!!
Wireshark training, Network analysis courses, Packet analysis training, Network security certification, Online Wireshark classes abuja lagos owerri portharcourt, Cybersecurity training programs abuja lagos owerri portharcourt, Network troubleshooting courses, Certified network analyst, Network forensics training abuja lagos owerri portharcourt, Wireshark certification abuja lagos owerri portharcourt, Network traffic analysis courses abuja lagos owerri portharcourt, Cybersecurity skills training, Packet capture training, Ethical hacking training abuja lagos owerri portharcourt, Network protocol analysis, IT security training, Cyber threat detection, Network monitoring training abuja lagos owerri portharcourt, Data packet inspection, Network performance optimization abuja lagos owerri portharcourt



